APT36 Explained: Transparent Tribe’s Tools, Targets & IOC's
- GK
- Sep 6, 2025
- 4 min read

🕵️♂️APT36—also known as Transparent Tribe, Mythic Leopard, ProjectM, and Earth Karkaddan—is a Pakistan-based advanced persistent threat (APT) group active since at least 2013. It is widely believed to operate in support of Pakistani state interests, with a primary focus on espionage against Indian defence, government, and diplomatic sectors.
Opportunistic attacks in Sri Lanka, Nepal, the US, and the UK.
Historically, APT36 emerged from a broader landscape of South Asian cyber conflict, where state-sponsored groups increasingly turned to digital espionage to gain strategic advantages. The group’s early campaigns were rudimentary, relying on basic phishing techniques and commodity malware.
Over the years, however, APT36 has matured significantly, adopting sophisticated tactics and developing custom malware families tailored to its targets.
APT36 has demonstrated a consistent ability to adapt its tooling and delivery mechanisms to bypass traditional security controls. Its campaigns often leverage geopolitical events to increase the success rate of social engineering attacks, making it a persistent threat to national security and critical infrastructure.
🎯 Target Profile
APT36 has evolved its tactics to target both Windows and Linux environments, with recent campaigns focusing on:
Indian Government entities
Defence personnel
Critical infrastructure
Educational institutions
Research organisations and think tanks
Diaspora communities and NGOs involved in human rights and regional policy advocacy
The group’s targeting strategy reflects a deep understanding of India’s socio-political landscape. By focusing on institutions that influence policy and public opinion, APT36 aims to gather intelligence that can be used to shape regional narratives and inform strategic decisions.
🧰 Tactics, Techniques, and Procedures (TTPs)
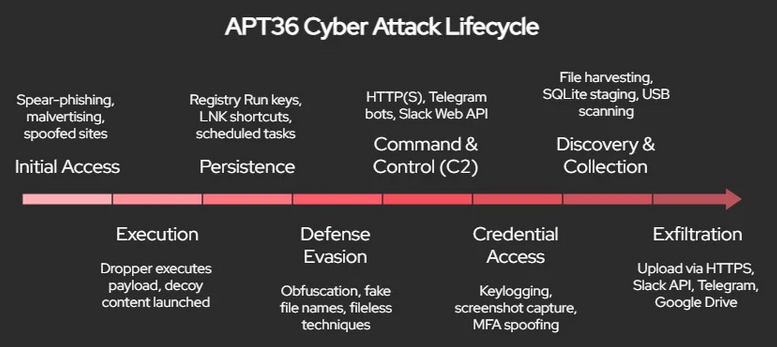
Initial Access
Spear-phishing emails with malicious Office documents (T1566.001)
Trojanised software installers, including fake Kavach 2FA apps
Phishing emails with RAR/ZIP attachments
Use of compromised legitimate websites to host payloads
Exploitation of zero-day vulnerabilities in document viewers
Execution
Malicious LNK files exploiting WinRAR and shortcut parsing flaws
Remote Access Trojans (RATs): Crimson RAT, ObliqueRAT
Use of PowerShell and batch scripts for payload delivery
Deployment of custom loaders and droppers
Persistence & Privilege Escalation
Registry Run keys and Startup folder persistence (T1547.001)
DLL sideloading
Scheduled tasks and service creation for long-term access
Exploitation of local privilege escalation vulnerabilities
Command & Control (C2)
HTTP/S-based C2 servers
Domains mimicking Indian government portals and NGOs
“Stealth Server” C2 panels running on port 8080
Use of dynamic DNS services to evade detection
Encrypted communication channels using custom protocols
Exfiltration & Objectives
Credential theft via keyloggers and browser scraping
Document exfiltration from shared drives and cloud storage
Webcam and microphone surveillance
Targeted data theft from defence-related research
Collection of intelligence on military operations and diplomatic communications
🧪 Recent Campaigns
Linux BOSS Exploitation
APT36 has begun targeting Indian BOSS Linux systems using weaponised .desktop shortcut files. These masquerade as PDFs but execute embedded commands upon launch, downloading ELF payloads. This marks a significant expansion in their targeting scope, indicating a deeper understanding of regional tech stacks and a willingness to diversify beyond Windows-based attacks.
These documents contained embedded macros and links to fake login pages, designed to harvest credentials from Indian government employees. The emotional manipulation and urgency embedded in these lures significantly increase click-through rates and demonstrate the group’s psychological operations capabilities.
🧬 Indicators of Compromise (IOCs)
IOC's can change daily, for the most up to date list use the live AlienVault report.
File Hashes
f03ac870cb91c00b51ddf29b6028d9ddf42477970eafa7c556e3a3d74ada25c9

55b7e20e42b57a32db29ea3f65d0fd2b2858aaeb9307b0ebbcdad1b0fcfd8059

55972edf001fd5afb1045bd96da835841c39fec4e3d47643e6a5dd793c904332

AlienVault - most recent
OpenCTI - most recent
Domains and IP Addresses
SuperPrimeServices[.]com
Advising-Receipts[.]com
FunDay24[.]ru
hXXps://superprimeservices[.]com/nishat/order/PO-003443125[.]df[.]7z

🌍 Geopolitical Implications
APT36’s operations are emblematic of the growing cyber capabilities of regional powers. The group’s alignment with Pakistani strategic interests suggests a broader trend of state-sponsored cyber espionage being used as a tool of foreign policy. By targeting Indian institutions, APT36 seeks to undermine trust, gather intelligence, and potentially disrupt critical operations.
The use of emotionally charged lures tied to real-world events indicates a sophisticated understanding of psychological warfare. These tactics not only compromise systems but also erode morale and trust within targeted organisations.
🛡️ Mitigation & Recommendations
Block known IOCs at perimeter and endpoint controls
Disable macros in Office documents by default
Monitor for unusual .desktop file executions in Linux environments
Use threat intelligence platforms like OpenCTI for aggregation and analysis
Educate users on phishing awareness, especially around emotionally charged or urgent themes
Implement behavioural analytics to detect anomalous RAT activity
Deploy endpoint detection and response (EDR) solutions with heuristic analysis
Conduct regular threat hunting exercises focused on APT36 TTPs
Rotate credentials frequently.
Use phishing-resistant MFA methods and verify MFA app authenticity.
Audit use of services like Telegram, Slack, and Google Drive on enterprise endpoints.
YARA Rule example
rule APT36_IOCs_Indicators{meta:author = “Cyfirma Research”description = “Detects known APT36-related indicators (hashes, IP, domains)”date = “2025-06-08”threat_group = “APT36 / Transparent Tribe”
strings:
// SHA256 file hashes (can be used for memory or file scan)$hash1 = “f03ac870cb91c00b51ddf29b6028d9ddf42477970eafa7c556e3a3d74ada25c9”$hash2 = “55b7e20e42b57a32db29ea3f65d0fd2b2858aaeb9307b0ebbcdad1b0fcfd8059”$hash3 = “55972edf001fd5afb1045bd96da835841c39fec4e3d47643e6a5dd793c904332”
// Domains used by APT36$domain1 = “SuperPrimeServices.com”$domain2 = “Advising-Receipts.com”$domain3 = “FunDay24.ru”$domain4 = “slotgacorterbaru.xyz”$domain5 = “servisyeni.xyz”$domain6 = “chillchad.xyz”$domain7 = “ggpoker.xyz”$domain8 = “boldcatchpoint.shop”$domain9 = “zhangthird.shop”$domain10 = “vipwin.buzz”$domain11 = “wholly-well.info”$domain12 = “rapio.site”$domain13 = “55cc.info”$domain14 = “megasofteware.net”$domain15 = “worrr19.sbs”$domain16 = “kp85.cyou”$domain17 = “mczacji.top”$domain18 = “59292406.xyz”
// IPs used by APT36$ip1 = “76.223.54.146”$ip2= “188.114.97.7”$ip3= “13.248.169.48”$ip4= “84.32.84.32”$ip5= “217.114.10.11”$ip6= “207.244.126.106”$ip7= “172.67.148.140”$ip8= “198.252.111.31”$ip9= “15.197.148.33”$ip10= “162.254.38.217”$ip11= “104.21.41.144”condition:any of ($hash*) or any of ($domain*) or any of ($ip*)}
🧾 Summary
APT36 represents a persistent and evolving threat to Indian national security. Its campaigns are technically sophisticated, psychologically manipulative, and geopolitically motivated. By understanding its tactics and implementing robust defensive measures, organisations can better protect themselves against this formidable adversary.
Credit to: https://socradar.io/dark-web-profile-apt36/







Comments